apple_connect
The validation server returns a Token object in the response body of a successful validation request. Use this endpoint to either authorize a user by validating the authorization code received by your app, or by validating an existing refresh token to verify a user session or obtain access tokens.
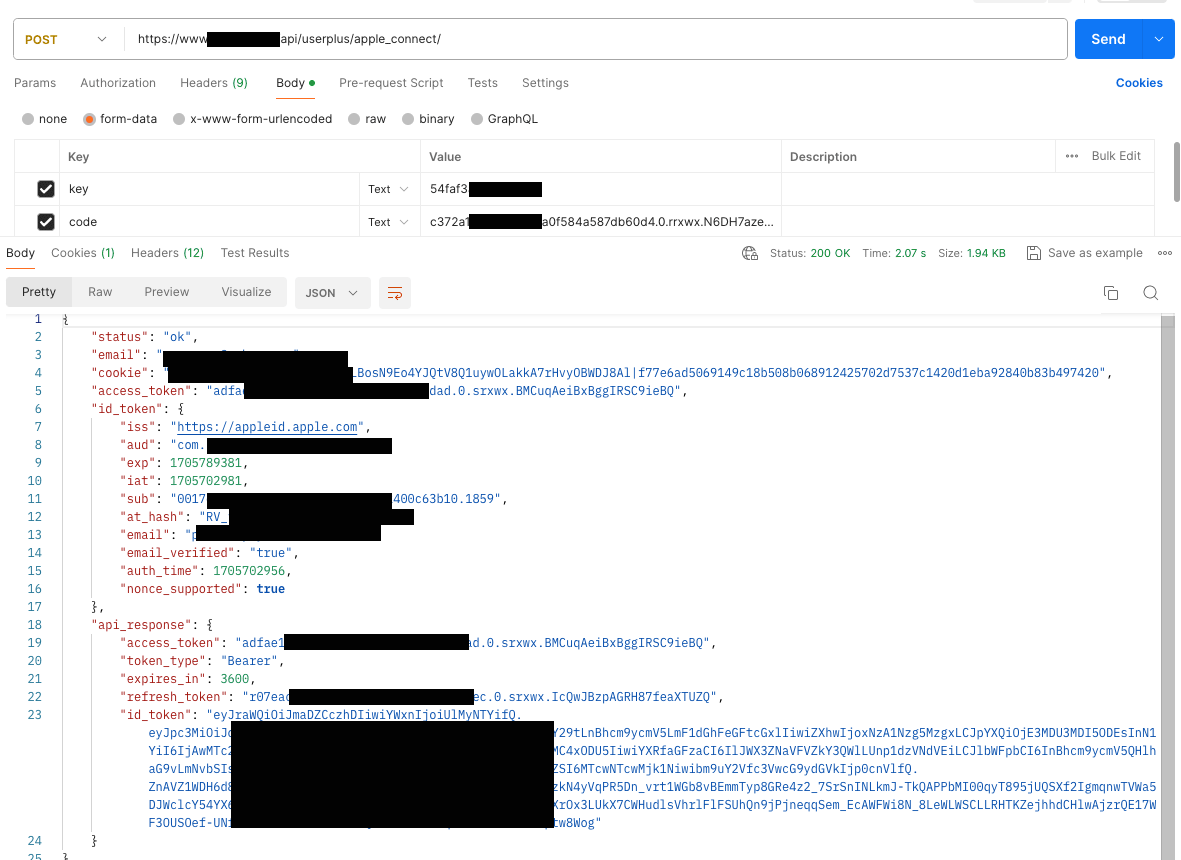
Screenshot of Postman API call example:
After the apple server validates the authorization code, the endpoint returns the identity token, an access token, and a refresh token. The following is an example authorization validation response.
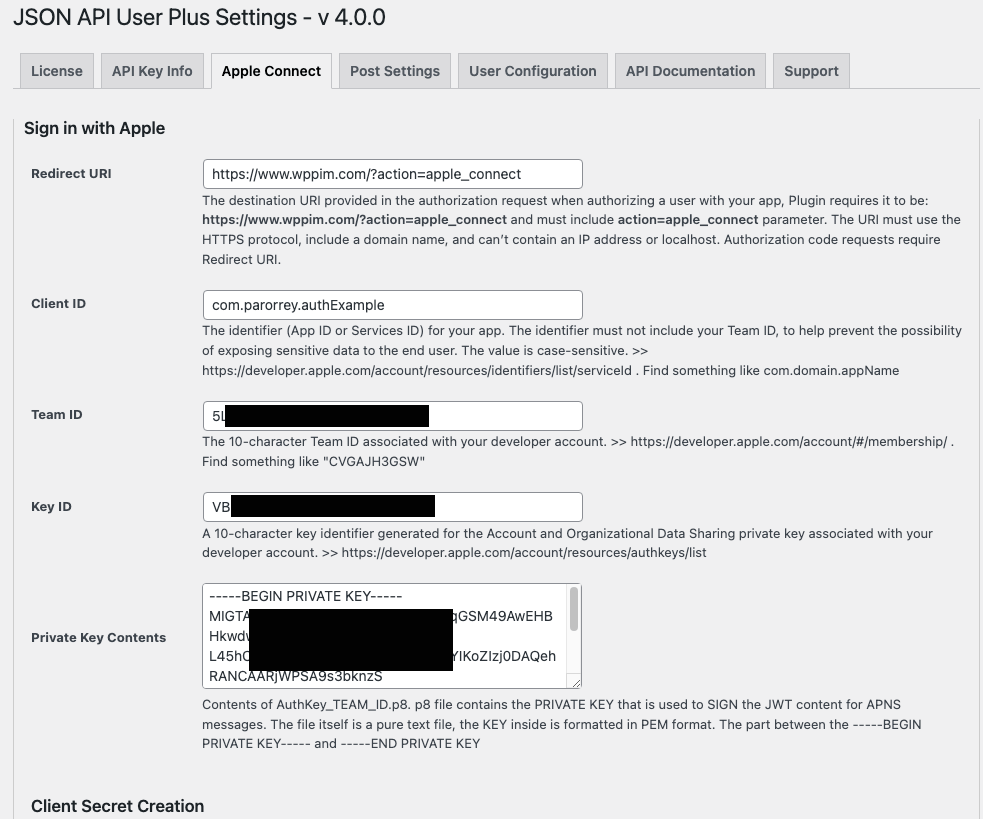
User Plus Apple Connect Settings
You will need to provide Redirect URI, Client ID, Team ID, Key ID and Private Key in the specified options in the plugin settings panel. A client secret will be generated based in these information and used to Apple REST API calls.
You can check the screenshot of Apple Connect Panel options of the User Plus plugin:
Redirect URI
The destination URI provided in the authorization request when authorizing a user with your app, Plugin requires it to be: https://www.domain.com/?action=apple_connect and must include action=apple_connect parameter. The URI must use the HTTPS protocol, include a domain name, and can’t contain an IP address or localhost. Authorization code requests require Redirect URI.
Client ID
The identifier (App ID or Services ID) for your app. The identifier must not include your Team ID, to help prevent the possibility of exposing sensitive data to the end user. The value is case-sensitive. >> https://developer.apple.com/account/resources/identifiers/list/serviceId . Find something like com.domain.appName
Team ID
The 10-character Team ID associated with your developer account. >> . Find something like “CVGAJH3GSW” on https://developer.apple.com/account/#/membership/
Key ID
A 10-character key identifier generated for the Account and Organizational Data Sharing private key associated with your developer account. >> https://developer.apple.com/account/resources/authkeys/list
Private Key
Contents of AuthKey_TEAM_ID.p8. p8 file contains the PRIVATE KEY that is used to SIGN the JWT content for APNS messages. The file itself is a pure text file, the KEY inside is formatted in PEM format. The part between the —–BEGIN PRIVATE KEY—– and —–END PRIVATE KEY
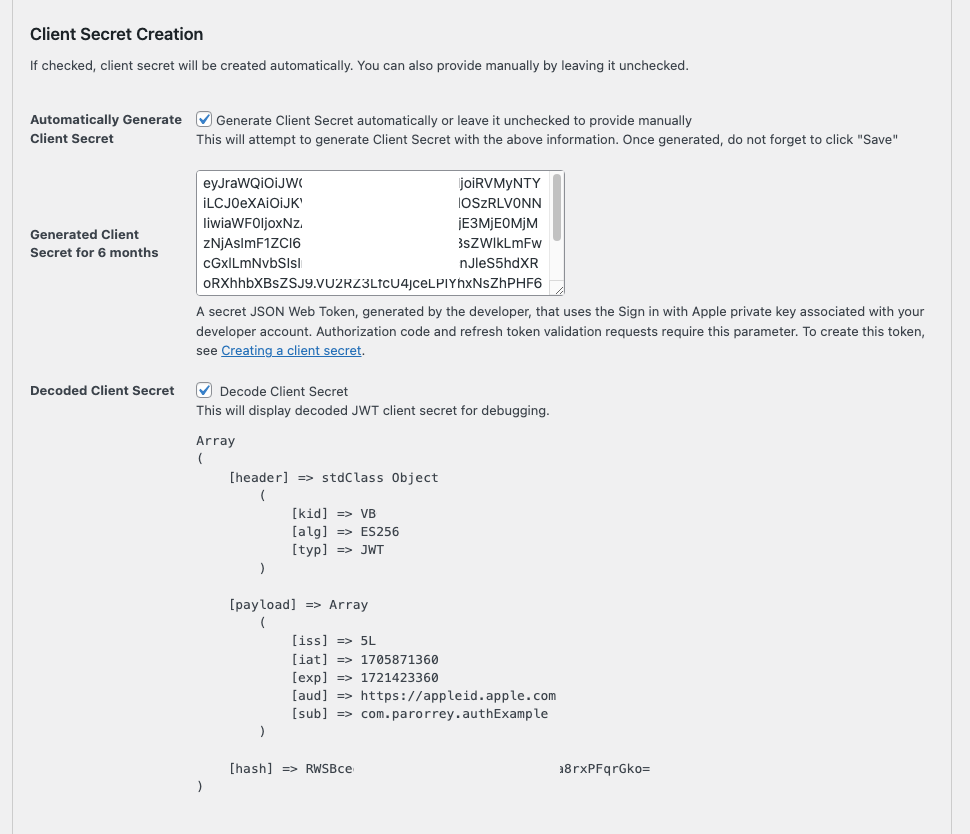
Client Secret Creation
If checked, client secret will be created automatically. You can also provide manually by leaving it unchecked.
Client Secret is a secret JSON Web Token, generated by the developer, that uses the Sign in with Apple private key associated with your developer account. Authorization code and refresh token validation requests require this parameter. To create this token, see Creating a client secret.
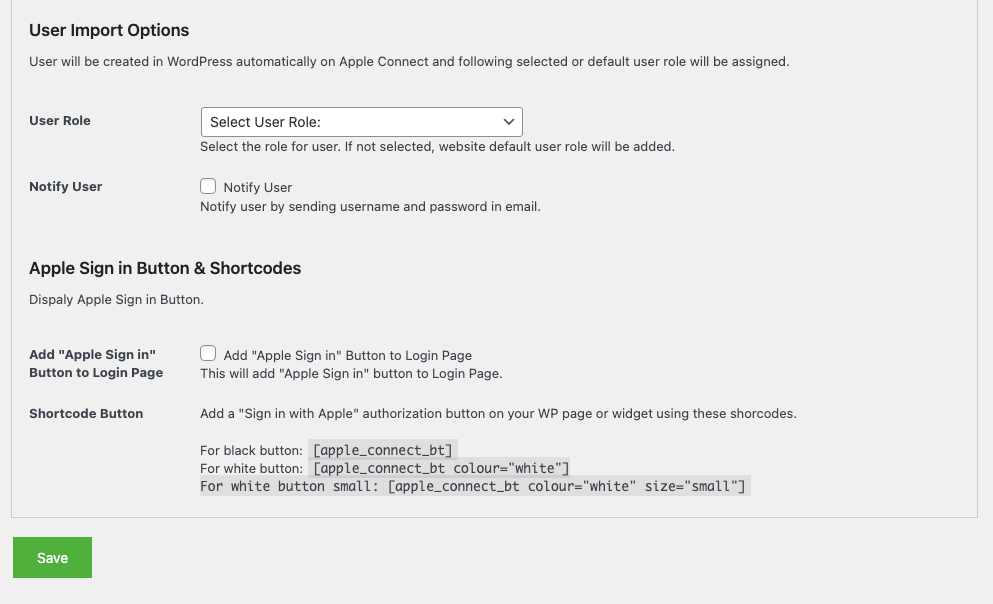
User Import Options for the WordPress website
User will be created in WordPress automatically on Apple Connect and following selected or default user role will be assigned. You can select the user role and option to notify the user for his account creation in the WordPress website.
These settings work for both REST API endpoints and Web frontend Login buttons to sign in Apple user.
These options also include Apple Sign in Button & Shortcodes to display in pages, posts and widgets and to add and display Apple Sign in Button on WordPress login screen.
Resource URL
https://www.domain.com/api/userplus/apple_connect/Method
Required Parameters
- key – get API key from Settings > User Plus
- code - Provide valid code generated with `apple_request_auth` endpoint
Optional Parameters
redirect_uri: https://www.domain.com/?action=app_receive
You will ned to receive POST information on this url yourself to further process the user data, email, access_token etc for your app.
Endpoint Returns
cookie - to use with other user related endpoints
email of user
access_token
id_token
api_response
Sample Request URL
https://www.domain.com/api/userplus/apple_connect/Sample Response
{
"status": "ok",
"email": "sample@email.com",
"cookie": "user|1706912...b83b497420",
"access_token": "adfae...dffBQ",
"id_token": {
"iss": "https://appleid.apple.com",
"aud": "com.domain.appExample",
"exp": 1705789381,
"iat": 1705702981,
"sub": "001767.....1859",
"at_hash": "RV_...MuQ",
"email": "sample@email.com",
"email_verified": "true",
"auth_time": 1705702956,
"nonce_supported": true
},
"api_response": {
"access_token": "adg61...67Or9",
"token_type": "Bearer",
"expires_in": 3600,
"refresh_token": "rca7...lABoQ",
"id_token": "eyJra...96sZg"
}
}